With the current cyber space era, cyber attacks are now more advanced than ever. From phishing mail to data breaches, individuals and institutions are more exposed to their private data. Perhaps the most influential yet unknown instrument in internet security is the proxy server. Placing itself between an end user and the world wide web, proxy servers provide degrees of protection, anonymity, and management that render them a vital instrument within the field of cyber security.
What is a Proxy Server?
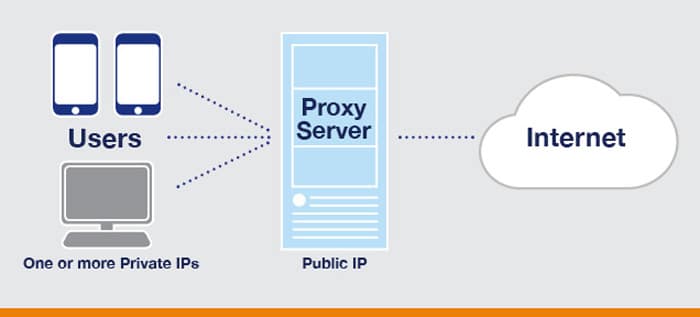
A proxy server is a go-between that comes between websites visited and users. Instead of the internet being accessed directly, requests are issued to go through the proxy server before sending the request to where it is supposed to go. Upon the website’s reply, the proxy returns the data to the user.
This is a simple process of redirecting that hides the user’s real IP address, giving both protection and anonymity. To users and corporations, proxies help create a safer web experience with less exposure to nefarious threats.
Why Proxy Servers Matter in Cyber Security
1. Enhanced Privacy and Anonymity
- Hides your original IP address.
- Shuts down websites and cyber attackers from accessing your location.
- Offers an additional degree of anonymity and makes actions more difficult to trace online.
For companies that deal with sensitive data, proxies prevent spear cyberattacks by masking employee IPs so internal activity remains private.
2. Cyber Threat Protection
Proxy servers can act as filters to prevent malicious content from reaching the user’s device even before it arrives. Most organizations implement proxies to detect and filter out:
- Malicious websites
- Suspect downloads
- Pop-ups and advertisements that could have malware
This advance filtering greatly reduces users’ chances of falling prey to phishing or ransomware attacks.
3. Secure Remote Access
The pandemic that has become reality in recent times forces remote work. Proxies are crucial in providing secure access to company networks. The company systems may be accessed by the employees using proxies that apply company encryption and authentication so that sensitive data is not at risk of being exposed while in transit.
4. Bandwidth Monitoring and Control
In addition to security, proxy servers can also allow IT admins to monitor and control bandwidth and monitor user activity. This benefits organizations with:
- Preventing access to dangerous websites by users without permission
- Saving bandwidth usage of non-business applications
- Tracking traffic patterns to determine suspicious activity that might indicate a breach
5. Encrypting Data for Secure Communication
Most proxy solutions are able to encrypt using SSL, which keeps sensitive data like login credentials, payment details, and private messages safe from interception by hackers.
Main Advantages for Businesses
Businesses are now constantly being bombarded with cyber attacks, from DDoS attacks to insider attacks. Proxy servers offer some advantages to businesses, which include:
- Data Loss Prevention: SSL proxies can be utilized to ensure that sensitive data does not leak outside the company network.
- Geo Restrictions: Businesses can bypass geo-blocks while conducting competitor analysis or market research.
- Scalability: Businesses utilize proxies in massive networks without affecting performance.
- Compliance with Regulation: Proxies operate to keep regulators at bay by providing data-handling protocols that are secure.
Real-World Applications of Proxy Servers in Cyber Security
- E-commerce Security: Payment information of customers is protected, and fraud is avoided by online retailers through proxies.
- Government Institutions: Proxies are employed in clandestine operations to prevent surveillance and conceal confidential data.
- Schools and Colleges: Proxies are employed by schools and colleges for monitoring students’ browsing and blocking distracting or malicious sites.
- Healthcare Infrastructures: Hospitals and clinics employ proxies to secure patient records and block unapproved data leakage.
Selecting the Correct Proxy Solution
With a number of proxy options to choose from—HTTP proxies, SOCKS proxies, and transparent proxies—you must choose the one that suits your needs best. Businesses and individuals must remember:
- Security Features: SSL encryption, malware filtering, and monitoring facilities.
- Performance: Can handle traffic without slowing down the network.
- Scalability: Adaptable enough to scale up in accordance with your business needs.
- Reputation of Provider: Opt for trustworthy providers that promise timely performance and security.
One such reliable platform is ObelysQ, which offers advanced solutions tailored to improving both security and privacy. Choosing a trusted provider ensures that you’re not only hiding your IP address but also enhancing your overall cybersecurity framework.
The Future of Proxy Servers in Cyber Security
As cyber attacks advance, proxy servers will play a vital role to guard online transactions more and more. With the use of artificial intelligence and machine learning, modern-day proxies are able to identify unusual patterns, block real-time attacks, and become immune to new threats.
In addition, amid cloud computing and work-from-home environments, safe proxies will get their share of maintaining far-away workers dispersed and guarding organizational assets.
Conclusion
Proxy servers are not just restriction-bypassing devices—these are crucial components of modern cyber security protocols. Granting privacy, security, and control, proxies enable individuals and businesses to protect themselves against constantly changing online threats.
From preventing dangerous content to protecting confidential data, proxies provide a cleaner and safer cyber space. As an individual who protects private information or a company that protects company assets, the employment of proxy technologies such as ObelysQ can be what means the difference between exposure and protection.